Visibility with the Admin Configuration Kit: Unleashing Potential
What is Visibility with Admin Configuration Kit?
Visibility with Admin Configuration Kit . Let’s set the scene. You’re an admin. You’ve talked to your users. You know what they want, informally, but you don’t know how to configure it. You don’t even know what you’re imaginary to configure!
Generally, at this point, you had started searching Google, Twitter, Help & Training, Trailhead, and the Trailblazer Community.
Visibility and Security Organization Kit:-
Our first Organization Kit focuses on security settings, object-level security, field-level security, and record access. If you are using Sales Cloud, Service Cloud, or building apps with the Salesforce stage, you will find useful prompts and recommendations in this release.
menu item in Setup that you require to configure.
The same is true for troubleshooting a point or error. It can be really difficult to be aware of what steps you need to take to resolve it.
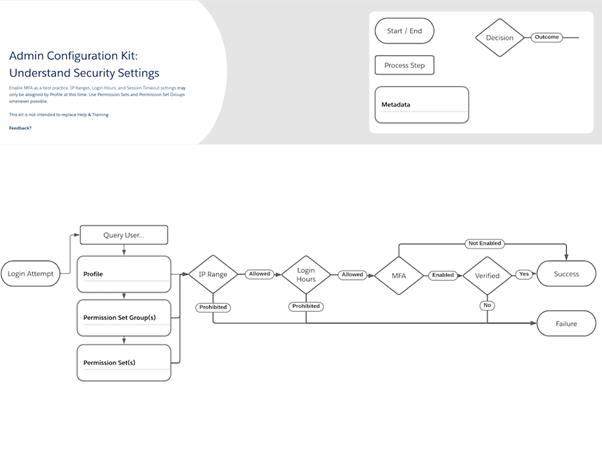
The visibility with Admin Configuration Kit has been built by admins for admins, but we want it to be as rare and impactful as potential. That means we want and need to hear from you to upgrade them.
How to ensure security in your Salesforce Org?
Setting the data that each user has access to is one of the key steps to secure safety and fearless in your Salesforce org. After everything has been implemented and your data model is in place, the next area of focus should be understanding your users’ activities and the level of access needed.
Believe and safety are at the top of Salesforce’s fundamental list. The stage has everything you need if you’re looking to raise a strong user security paradigm. However, this security approach has flaws that an offensive can utilize to gain access to your data. The Salesforce Architect has the due to secure that these features are set up properly.
Design security in Salesforce is an architecture that is maintainable while ensuring that users can only access what they need to complete their work.
When most people think of security they think of authentication or gaining access to a system. This is a critical part of system security, but it is just the start. In addition, it is necessary to note that Objects, Fields, and records are all types of data in Salesforce. An extensive Salesforce security data model is required to protect the many individuals and data that are in the system.
Data access: -
In Salesforce, Securing Data from unauthenticated users is very important. Data in Salesforce is picked in the form of Objects, Fields, and records. To Secure data, we have to design and implement a salesforce security data model for all different users and the data they need to access. We have four different levels of data access on Salesforce.com.
- Organizational or
- system-level security.
- Object-level security.
- Field-level security.
- Record-level security.
DATA SECURITY MODEL IN SALESFORCE:-
1. Organizational or system-level security:-
For your overall setup, you can keep up a list of approved users, set password approaches, and limit logins to particular hours and/or areas.
Salesforce’s highest degree of security is its system level, where you put a list of allowed users, password regulations, login IP ranges, limiting login access to particular hours, Session Security, Login Flows, and Network Access restrictions.
System level security is the highest level of security in Salesforce where we maintain a list of authorized users to log in, Password policies, Login IP ranges, limiting login access to certain hours, Session Security, Login Flows, and Network Access.
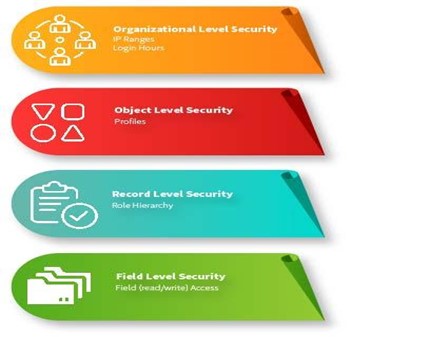
2. Object-level Security :-
Access to object-level data is the easiest way thing to control. By setting consent on a specific sort of item, you can keep a gathering of users from creating, viewing, altering, or erasing any records of that object. For instance, you can utilize object authorizations to guarantee that interviewers can see positions and employment applications but not alter or erase them.
A profile or permission set-based perspective to Object Security in Salesforce involves assigning permissions to particular objects such as Accounts, Contacts, or Opportunities. You can allow the user access to editing, creating, deleting, or viewing records in that object.
Object Level Security, also known as Profile Level Security, is a standard method to redress data thieves in Salesforce. Today, we will discuss it to give you better clarity of the same.
Object Level Security in Salesforce is done at the profile level by setting permissions on Objects. We can prevent users from Edit, Creating, Deleting, or Viewing a record in that Object.
In Salesforce, profiles control access to the object level and field-level security among elective things like applications, tabs, etc. Since Jenny is a recruit, the fellow administrator needs to add Jenny to the Eligible profile that has access to the sales applications and related items to begin giving her access to the Salesforce information.
How does Salesforce permit field-level security?
Aside from the access level of the field, Salesforce permits field-level security by setting some field characters as given below: individual property: If this wealth is checked then salesforce keeps that field from duplicates.
3. Field-level security:-
In Salesforce, field-level security is a setting that allows administrators to control who has an approach to certain organizational details. The administrator can select which profiles or permission sets have an approach to view, update, and save data in particular fields. Everybody in the organization does not every time have access to all of Salesforce’s data. Depending on the users that expect it, certain data must be kept restricted. This is also a great path to clarify a user’s view by removing visibility to fields that they don’t need for their job. You can also receive fields off of page layouts and other views, but then the user be able still to view these fields when creating reports or list views.
You can also accept fields off of page layouts and other views, but then the user may static see these fields when creating reports or list views.
Field-level security is a setting that gives over Salesforce admins to define user restrictions as to who can access particular org data. The setting lets the admin control which user profiles can view, edit, and save information on particular fields.
Your Salesforce org contains lots of data, but you maybe don’t want each field accessible to everyone.
How to enable field-level permissions in Salesforce?
If you enable both visible & read-only, then the user can only see that field, he can edit. By using the view field accessibility button. Go to the field you want to enable field-level permissions and click on the view field accessibility button. then you will negotiate to the down screen.
4. Record-level Security:-
You can allow specific users to see an item, so far then limit the personal article records that they are permitted to view. For instance, an interviewer can view and alter her surveys, but so far not the audits of different interviewers. You can look after record-level access in these four different ways.
In Salesforce, when you have to authorize access to particular records within the object, it is done with the help of Record-level security. For example, object-level security says a User can view Contacts, but record-level security controls whether or not they can view the record for John Doe. Record-level security is overdone by most things – profiles, permission sets, sharing rules, sharing settings, role hierarchy, and even apex and manual record sharing. Record-level security cannot override object-level or field-level security, so if someone doesn’t have permission to Opportunities at the object level, it doesn’t work if you set up a sharing rule to share certain Opportunities with them.
Conclusion: -
Complex security models are more challenging to maintain and more effective for security vulnerabilities. large preposition, the execution of a platform can be minus impacted by composite security approaches. The best thing to avoid this security is to work with a solid governance system.
Secure your data is of the greatest importance. Salesforce understands this and that is why as already demonstrated above, it provides various ways in which you can keep your data controlled. Here, in this blog, we discussed in detail the security model Salesforce, Salesforce security model diagram, and Salesforce security model best practices. By understanding the Salesforce Data Security model, you can ensure the greater safety of your data.


